Do you need a series random unique numbers for scratchcards, or bundle codes for vouchers?
There are many ways to do this work, in this articles I would like to share a way to generate these numbers in SQL server.
SQL server has a function calling NEWID(), it creates a unique GUID (uniqueidentifier) value. Depending on your purpose, you can use this function in several ways to generate unique numbers.
Generate a GUID:
SELECT NEWID()
It will generate a new random uniqueidentifier e.g. 4FEC77B5-83AC-485B-9B0A-9A3E58BE4A06
Generate a random unique number:
SELECT ABS(CAST(CAST(NEWID() AS VARBINARY(5)) AS Bigint))
It will generate a random unique number e.g. 685690842599
Generate a random unique number with fixed digit:
SELECT REPLACE(STR(CAST(CAST(NEWID() AS binary(6)) AS bigint),15),0,0)
You will have a random unique number with fixed digit e.g. 188125385042097. Then you can use it for your scratchcard or voucher etc.
That's all. Any comment is welcome!
Wednesday, December 24, 2014
Friday, November 28, 2014
Windows Server: prevent anonymous login and ban IP of attacker
On Windows Server 2008 R2 / Windows Server 2012 you can disable anonymous login by using Local Group Policy Editor. To open the Local Group Policy Editor: click Start button, key gpedit.msc in the Start Search box, and then press ENTER.
Under Computer Configuration\Windows Settings\SecuritySettings\Local Policies\SecurityOptions, there are 6 policies to control what information can be accessed anonymously:
1. Network access: Allow anonymous SID/Name translation
2. Network access: Do not allow anonymous enumeration of SAM accounts
3. Network access: Do not allow anonymous enumeration of SAM accounts and shares
4. Network access: Let Everyone permissions apply to anonymous users
5. Network access: Named Pipes that can be accessed anonymously
6. Network access: Shares that can be accessed anonymously
Just disable policy 1 and 4, enable policy 2 and 3, and clear empty for policy 5 and 6.
Disabling anonymous login is not enough for preventing attempts to attack your Windows Server, you should buying & install an application like Symantec Endpoint Protection to protect your server with advance functions.
However if your server just run SQL server and you use Remote Desktop to remote the server, you can do a security layer by your self. The first thing is you should change the default service port of Remote Desktop and SQL server. The second thing is you should use IPBan written by Jeffrey N. Johnson, it is a free tool tracking any IP that invokes services on your server and when number of fail events reaches to a predefined threshold, it will block the IP in the Windows Advanced Firewall by using a Blocking rule there.
If you like coding, you can download the code of IPBan from here. If not, you can download its binary from here (required .NET Framework 4). Below are main configurations for making it up & run:
1. Config Remote Desktop Session Host Configuration to log IP address in event log. To run it: click Start button, key Remote Desktop Session Host Configuration in the Start Search box, and then press ENTER. Double click the connection RDP-Tcp to change encryption settings to native RDP encryption. See the picture below for howto. After finishing, please reboot your server.
2. Copy IPBan binary to a folder, e.g. D:\IPBan. Then open and modify IPBan.exe.config file. Below are some rules that you should learn:
2.1 Group rules, for example:
<Group>
<Keywords>0x90000000000000</Keywords>
...
<XPath>//Provider[@Name='MSSQLSERVER']</XPath>
...
</Group>
This group is used for tracking Application events for logging on to MS SQL server which having keyword 0x90000000000000, see the following captured image in Application events for more detail:
In this case, Provider is MSSQL$SGSQL2012, so we'll change MSSQLSERVER to MSSQL$SGSQL2012.
2.2 Rule for attempts before banning
<add key="FailedLoginAttemptsBeforeBan" value="5" />
2.2 Ban time rule (DD:HH:MM:SS)
<add key="BanTime" value="00:00:30:00" />
2.2 Log file rotation rule
<target name="logfile" xsi:type="File" fileName="${basedir}\logfile.txt" archiveNumbering="Sequence" archiveEvery="Day" maxArchiveFiles="28" />
3. Create IPBan service and start it
#sc create IPBan type= own start= auto binPath= D:\IPBan\ipban.exe DisplayName= IPBan
#net start IPBan
That's all. Now you can monitor your server under your way.
Any comment is welcome!
Under Computer Configuration\Windows Settings\SecuritySettings\Local Policies\SecurityOptions, there are 6 policies to control what information can be accessed anonymously:
1. Network access: Allow anonymous SID/Name translation
2. Network access: Do not allow anonymous enumeration of SAM accounts
3. Network access: Do not allow anonymous enumeration of SAM accounts and shares
4. Network access: Let Everyone permissions apply to anonymous users
5. Network access: Named Pipes that can be accessed anonymously
6. Network access: Shares that can be accessed anonymously
Just disable policy 1 and 4, enable policy 2 and 3, and clear empty for policy 5 and 6.
Disabling anonymous login is not enough for preventing attempts to attack your Windows Server, you should buying & install an application like Symantec Endpoint Protection to protect your server with advance functions.
However if your server just run SQL server and you use Remote Desktop to remote the server, you can do a security layer by your self. The first thing is you should change the default service port of Remote Desktop and SQL server. The second thing is you should use IPBan written by Jeffrey N. Johnson, it is a free tool tracking any IP that invokes services on your server and when number of fail events reaches to a predefined threshold, it will block the IP in the Windows Advanced Firewall by using a Blocking rule there.
If you like coding, you can download the code of IPBan from here. If not, you can download its binary from here (required .NET Framework 4). Below are main configurations for making it up & run:
1. Config Remote Desktop Session Host Configuration to log IP address in event log. To run it: click Start button, key Remote Desktop Session Host Configuration in the Start Search box, and then press ENTER. Double click the connection RDP-Tcp to change encryption settings to native RDP encryption. See the picture below for howto. After finishing, please reboot your server.
2. Copy IPBan binary to a folder, e.g. D:\IPBan. Then open and modify IPBan.exe.config file. Below are some rules that you should learn:
2.1 Group rules, for example:
<Group>
<Keywords>0x90000000000000</Keywords>
...
<XPath>//Provider[@Name='MSSQLSERVER']</XPath>
...
</Group>
This group is used for tracking Application events for logging on to MS SQL server which having keyword 0x90000000000000, see the following captured image in Application events for more detail:
In this case, Provider is MSSQL$SGSQL2012, so we'll change MSSQLSERVER to MSSQL$SGSQL2012.
2.2 Rule for attempts before banning
<add key="FailedLoginAttemptsBeforeBan" value="5" />
2.2 Ban time rule (DD:HH:MM:SS)
<add key="BanTime" value="00:00:30:00" />
2.2 Log file rotation rule
<target name="logfile" xsi:type="File" fileName="${basedir}\logfile.txt" archiveNumbering="Sequence" archiveEvery="Day" maxArchiveFiles="28" />
3. Create IPBan service and start it
#sc create IPBan type= own start= auto binPath= D:\IPBan\ipban.exe DisplayName= IPBan
#net start IPBan
That's all. Now you can monitor your server under your way.
Any comment is welcome!
Monday, October 20, 2014
Plugin to make Wordpress work with SQL server
If your website is using Windows server with IIS + SQL server and you want to have a blog using Wordpress, you may not want to install MySQL server on your existing server because it can make your server heavier and slower. Luckily there is a solution to make Wordpress work with your existing SQL server. Below are articles that can help you in details:
Installing WordPress on Windows using SQL Server 2008 R2 Part 1 - This section will cover installing and configuring PHP and IIS 7.5.
Installing WordPress on Windows using SQL Server 2008 R2 Part 2 - This section will cover configuring your SQL Server and installing and configuring WordPress.
The heart of this solution is wp-db-abstraction plugin, The following fixes can make it work more smoothly:
1. Open file wp-includes\wp-db.php, goto line 1294:
mysql_free_result( $this->result );
and change it to:
sqlsrv_free_stmt( $this->result );
This will help to flush out the resources after querying results. In this case we use sqlsrv function instead of mysql function
2. Open file wp-content\mu-plugins\wp-db-abstraction\translations\sqlsrv\translations.php, change:
$pattern = '/LIMIT\s*(\d+)((\s*,?\s*)(\d+)*)(;{0,1})$/is';
to
$pattern = '/LIMIT\s*(\d+)((\s*,?\s*)(\d+)*);{0,1}$/is';
In this file too, move to the function translate_specific($query), change it to the following code:
function translate_specific($query)
{
$tmp = strtoupper ("SELECT COUNT(NULLIF(`meta_value` LIKE '%\"administrator\"%', FALSE)), "
. "COUNT(NULLIF(`meta_value` LIKE '%\"editor\"%', FALSE)), "
. "COUNT(NULLIF(`meta_value` LIKE '%\"author\"%', FALSE)), "
. "COUNT(NULLIF(`meta_value` LIKE '%\"contributor\"%', FALSE)), "
. "COUNT(NULLIF(`meta_value` LIKE '%\"subscriber\"%', FALSE)), "
. "COUNT(*) FROM " . $this->prefix . "usermeta WHERE meta_key = '" . $this->prefix . "capabilities'");
if (strtoupper($this->preg_original) == $tmp) {
$query = "SELECT
(SELECT COUNT(*) FROM " . $this->prefix . "usermeta WHERE meta_key = '" . $this->prefix . "capabilities' AND meta_value LIKE '%administrator%') as ca,
(SELECT COUNT(*) FROM " . $this->prefix . "usermeta WHERE meta_key = '" . $this->prefix . "capabilities' AND meta_value LIKE '%editor%') as cb,
(SELECT COUNT(*) FROM " . $this->prefix . "usermeta WHERE meta_key = '" . $this->prefix . "capabilities' AND meta_value LIKE '%author%') as cc,
(SELECT COUNT(*) FROM " . $this->prefix . "usermeta WHERE meta_key = '" . $this->prefix . "capabilities' AND meta_value LIKE '%contributor%') as cd,
(SELECT COUNT(*) FROM " . $this->prefix . "usermeta WHERE meta_key = '" . $this->prefix . "capabilities' AND meta_value LIKE '%subscriber%') as ce,
COUNT(*) as c FROM " . $this->prefix . "usermeta WHERE meta_key = '" . $this->prefix . "capabilities'";
$this->preg_data = array();
}
if (stristr($query, "SELECT DISTINCT TOP 50 (" . $this->prefix . "users.ID) FROM " . $this->prefix . "users") !== FALSE) {
$query = str_ireplace(
"SELECT DISTINCT TOP 50 (" . $this->prefix . "users.ID) FROM",
"SELECT DISTINCT TOP 50 (" . $this->prefix . "users.ID), user_login FROM", $query);
}
if (stristr($query, 'INNER JOIN ' . $this->prefix . 'terms USING (term_id)') !== FALSE) {
$query = str_ireplace(
'USING (term_id)',
'ON ' . $this->prefix . 'terms.term_id = ' . $this->prefix . 'term_taxonomy.term_id', $query);
}
return $query;
}
I believe that you can have a Wordpress blog work with your existing SQL server soon -:) Any comment is welcome.
Installing WordPress on Windows using SQL Server 2008 R2 Part 1 - This section will cover installing and configuring PHP and IIS 7.5.
Installing WordPress on Windows using SQL Server 2008 R2 Part 2 - This section will cover configuring your SQL Server and installing and configuring WordPress.
The heart of this solution is wp-db-abstraction plugin, The following fixes can make it work more smoothly:
1. Open file wp-includes\wp-db.php, goto line 1294:
mysql_free_result( $this->result );
and change it to:
sqlsrv_free_stmt( $this->result );
This will help to flush out the resources after querying results. In this case we use sqlsrv function instead of mysql function
2. Open file wp-content\mu-plugins\wp-db-abstraction\translations\sqlsrv\translations.php, change:
$pattern = '/LIMIT\s*(\d+)((\s*,?\s*)(\d+)*)(;{0,1})$/is';
to
$pattern = '/LIMIT\s*(\d+)((\s*,?\s*)(\d+)*);{0,1}$/is';
In this file too, move to the function translate_specific($query), change it to the following code:
function translate_specific($query)
{
$tmp = strtoupper ("SELECT COUNT(NULLIF(`meta_value` LIKE '%\"administrator\"%', FALSE)), "
. "COUNT(NULLIF(`meta_value` LIKE '%\"editor\"%', FALSE)), "
. "COUNT(NULLIF(`meta_value` LIKE '%\"author\"%', FALSE)), "
. "COUNT(NULLIF(`meta_value` LIKE '%\"contributor\"%', FALSE)), "
. "COUNT(NULLIF(`meta_value` LIKE '%\"subscriber\"%', FALSE)), "
. "COUNT(*) FROM " . $this->prefix . "usermeta WHERE meta_key = '" . $this->prefix . "capabilities'");
if (strtoupper($this->preg_original) == $tmp) {
$query = "SELECT
(SELECT COUNT(*) FROM " . $this->prefix . "usermeta WHERE meta_key = '" . $this->prefix . "capabilities' AND meta_value LIKE '%administrator%') as ca,
(SELECT COUNT(*) FROM " . $this->prefix . "usermeta WHERE meta_key = '" . $this->prefix . "capabilities' AND meta_value LIKE '%editor%') as cb,
(SELECT COUNT(*) FROM " . $this->prefix . "usermeta WHERE meta_key = '" . $this->prefix . "capabilities' AND meta_value LIKE '%author%') as cc,
(SELECT COUNT(*) FROM " . $this->prefix . "usermeta WHERE meta_key = '" . $this->prefix . "capabilities' AND meta_value LIKE '%contributor%') as cd,
(SELECT COUNT(*) FROM " . $this->prefix . "usermeta WHERE meta_key = '" . $this->prefix . "capabilities' AND meta_value LIKE '%subscriber%') as ce,
COUNT(*) as c FROM " . $this->prefix . "usermeta WHERE meta_key = '" . $this->prefix . "capabilities'";
$this->preg_data = array();
}
if (stristr($query, "SELECT DISTINCT TOP 50 (" . $this->prefix . "users.ID) FROM " . $this->prefix . "users") !== FALSE) {
$query = str_ireplace(
"SELECT DISTINCT TOP 50 (" . $this->prefix . "users.ID) FROM",
"SELECT DISTINCT TOP 50 (" . $this->prefix . "users.ID), user_login FROM", $query);
}
if (stristr($query, 'INNER JOIN ' . $this->prefix . 'terms USING (term_id)') !== FALSE) {
$query = str_ireplace(
'USING (term_id)',
'ON ' . $this->prefix . 'terms.term_id = ' . $this->prefix . 'term_taxonomy.term_id', $query);
}
return $query;
}
I believe that you can have a Wordpress blog work with your existing SQL server soon -:) Any comment is welcome.
Monday, September 8, 2014
Facebook apps: new way is easier to create apps
Facebook has announced recently its process for developers integrating apps into the social network. The new process is easier than old process.
You can read here to know this new way.
Quote:
Thanks for your reading, welcome any comment.
Best regards.
You can read here to know this new way.
Quote:
In the original app-creation flow, you had to find and download our latest SDKs, create a Facebook App ID, enable the platform you were building for, and then copy and paste certain information between our docs and your development environment — all while trying to read our documentation. We are always trying to improve the experience for developers, and having a quick start to integrating with Facebook is one example.
In the new app registration flow, we've drastically simplified the experience and we added interactive guides to lead you through the process of integrating an app with Facebook. Now, we will only display the steps relevant to your app. Additionally, SDK downloads are included inline, along with code you can copy and paste into your app.Developers working on Windows Phone and Facebook Page Tabs apps can still access the older app creation tools by using the “advanced setup” link.
Thanks for your reading, welcome any comment.
Best regards.
Thursday, August 14, 2014
Amazon EC2: enable ICMP ping request
Amazon EC2 and its installed Windows doesn't allow ICMP ping requests by default. But you can enable this easily via the following steps:
If you don't see it there, can add it by the command line:
netsh advfirewall firewall add rule name="ALL ICMP V4" protocol=icmpv4:8,any dir=in action=allow
Now you can ping to your instance.
Welcome any comments and questions.
Best regards.
1. Allow ICMP ping request in Windows Firewall
Open Windows Firewall and enable ALL ICMP V4 inbound rule, blow is an example from Windows Server 2012r2:If you don't see it there, can add it by the command line:
netsh advfirewall firewall add rule name="ALL ICMP V4" protocol=icmpv4:8,any dir=in action=allow
2. Add inbound rule to Security Group of EC2
Let open the Secuirty Group of your instance on EC2, then add new inbound rules (Custom ICMP Rule / Echo Request) for your specific IP addresses (not recommend to allow all IP addresses), see below for example:Now you can ping to your instance.
Welcome any comments and questions.
Best regards.
Thursday, August 7, 2014
MySQL: swap valúes of 2 columns
If you want to swap values of 2 columns (e.g. col1 and col2) in a table (e.g. a_table), you can use below SQL:
UPDATE a_table SET col1=(@temp:=col1), col1 = col2, col2 = @temp;
Do you have another ways? Pls post comment here. Thanks!
UPDATE a_table SET col1=(@temp:=col1), col1 = col2, col2 = @temp;
Do you have another ways? Pls post comment here. Thanks!
Tuesday, July 29, 2014
Moving Blogger to joomla
Joomla is a powerful CMS, it lets you make your website/blog running in your way with professional look and feel. And you may have dozen reason to migrate your blog from blogger.com to Joomla if you know Joomla and you have an existing blog on blogger.com.
In this article, I'll share you my experience when I migrated my blog to Joomla. First of all, you should have a plan and overview SOP. Below is my simple SOP:
After installing, open menu Extensions >> Plugin Manager then enable FeedGator - Joomla Native Content Plugin. Before importing, you should create a category for imported articles. Go to Content >> Category Manager ans create one (e.g. Joomla!). Now it's time to add the feed of your blog. Open Components >> Feed Gator >> Manage Feeds, click New button to add new feed. Below is a sample screen shot:
In which, Feed URL is gotten from the RSS feed at the bottom of your blog where has Subscribe to: Posts (Atom) link. In above picture, it is my blog RSS feed: http://blog.vivavivu.com/feeds/posts/default. The next is Publishing tab, you can set as the following:
In Text Handling tab, remember to choose Get Source Full Text as Yes.
If you want to download images to Joomla website, let set as below in Images and Enclosures tab:
Because you migrate your blog, so let link back (track back) option in Links tab as No:
You can change another configurations if needing, then click Save & Close button. To import, select the feed which is just created, then click Import button, see the following picture for example:
If your blog don't have private domain/sub domain, let configure a private domain/sub domain for it before you migrate. Keep your blog run at least 2 weeks on the private domain/sub domain, it helps Google migrate rankings from its blogspot.com to this private domain/sub domain (e.g. blogger.yourdomain.com).
There are 2 cases for this situation:
<configuration>
<system.webServer>
<rewrite>
<rules>
<rule name="Redirect to new URL" stopProcessing="true">
<match url="^oldURL$" />
<conditions>
<add input="{HTTP_HOST}" pattern="^blogger\yourdomain\.com$" />
</conditions>
<action type="Redirect" url="http:/joomla.yourdomain.com/newURL" />
</rule>
</rules>
</rewrite>
</system.webServer>
</configuration>
5. Use this tool to check old URLs, make sure that them are redirected 301 correctly.
In this article, I'll share you my experience when I migrated my blog to Joomla. First of all, you should have a plan and overview SOP. Below is my simple SOP:
1. Prepare new Joomla website
I like Joomla 3.x, so I installed latest Joomla version with blank content. Then I choose a template that I love then install it to the new Joomla site.2. Export / Import content from Blogger to Joomla
There are many ways to do this. You can export XML content from Blogger then import it to Joomla. However I prefer to use FeedGator component to import articles from Blogger to Joomla. FeedGator is free component and you can download here. It imports RSS feedsinto your Joomla! database as content items. It supports full text importing. For Joomla 3.x, you should download FeedGator 3.0 alpha3. Although it is in test phase but you can use it for this importing purpose with my fix here.After installing, open menu Extensions >> Plugin Manager then enable FeedGator - Joomla Native Content Plugin. Before importing, you should create a category for imported articles. Go to Content >> Category Manager ans create one (e.g. Joomla!). Now it's time to add the feed of your blog. Open Components >> Feed Gator >> Manage Feeds, click New button to add new feed. Below is a sample screen shot:
In which, Feed URL is gotten from the RSS feed at the bottom of your blog where has Subscribe to: Posts (Atom) link. In above picture, it is my blog RSS feed: http://blog.vivavivu.com/feeds/posts/default. The next is Publishing tab, you can set as the following:
In Text Handling tab, remember to choose Get Source Full Text as Yes.
If you want to download images to Joomla website, let set as below in Images and Enclosures tab:
Because you migrate your blog, so let link back (track back) option in Links tab as No:
You can change another configurations if needing, then click Save & Close button. To import, select the feed which is just created, then click Import button, see the following picture for example:
3. Organize new content on Joomla
After importing content from your blog to Joomla, let check the imported content, imported images. You may edit a little to adapt your articles with new template on Joomla. You may change the structure of menus etc.4. Redirect 301 old URLs on Blogger to new URLs on Joomla
To keep Google ranking for your articles, you should make 301 redirection from old URLs on Blogger to new URLs on Joomla.If your blog don't have private domain/sub domain, let configure a private domain/sub domain for it before you migrate. Keep your blog run at least 2 weeks on the private domain/sub domain, it helps Google migrate rankings from its blogspot.com to this private domain/sub domain (e.g. blogger.yourdomain.com).
There are 2 cases for this situation:
- You want to keep current domain (blogger.yourdomain.com).
- You want to move to new domain (e.g. joomla.yourdomain.com)
4.1 Keep current domain
There are many solutions, below is my way:- Move your old blogger domain (blogger.yourdomain.com) to a real host (support PHP + MySQL)
- Install Joomla for the domain
- Import old content to a category
- Use Redirect component of Joomla (menu Components >> Redirect) to redirect all old URLs to new URLs
- After 2 weeks, let check Google search
4.2 Move to new domain
Below are steps:- Install new Joomla on another domain/sub domain (e.g. joomla.yourdomain.com).
- Import old content to new Joomla website
- Move your old blogger domain (blogger.yourdomain.com) to a real host (e.g. Windows server + IIS + URL Rewrite)
- Redirect 301 all old URLs to new URLs on joomla.yourdomain.com. In the case of you use IIS and URL Rewrite module, here is an example:
<configuration>
<system.webServer>
<rewrite>
<rules>
<rule name="Redirect to new URL" stopProcessing="true">
<match url="^oldURL$" />
<conditions>
<add input="{HTTP_HOST}" pattern="^blogger\yourdomain\.com$" />
</conditions>
<action type="Redirect" url="http:/joomla.yourdomain.com/newURL" />
</rule>
</rules>
</rewrite>
</system.webServer>
</configuration>
6. Keep these re-directions at least 2 weeks for Google transfering its rankings to new URLs
7. Check Google search and turn off your old blog if you see OK.
Thanks for reading! Your comments and questions, and shares are welcomed and appreciated! Do you have a blog?
Thanks for reading! Your comments and questions, and shares are welcomed and appreciated! Do you have a blog?
Saturday, July 12, 2014
Fast way to rename or create .htaccess file on Windows Vista and later
From Windows Vista, it doesn't allow us to create a file which its name has only file extension and empty file name (e.g. .htaccess file). If you do, it will inform "You must type a file name".
Below is a trick to solve this problem.
1. Open Windows Explorer.
2. Right click >> New >> Text Document
3. Enter the extension name with dot at the end (e.g .htaccess.)
4. Confirm Yes for the warning
5. Congrat, now you got the wanted file -:)
If you know any other ways, pls give me comments below. Welcome!
Below is a trick to solve this problem.
1. Open Windows Explorer.
2. Right click >> New >> Text Document
3. Enter the extension name with dot at the end (e.g .htaccess.)
4. Confirm Yes for the warning
5. Congrat, now you got the wanted file -:)
If you know any other ways, pls give me comments below. Welcome!
Thursday, June 26, 2014
Joomla: plugin for enhancing security rule on login and password
If you are using Joomla, you may want to protect your administrator area from eyes of bad guys, and you may also want to lock an user after some times of failed login. This help your users and website more secure under attacks of hackers in order to stolen your users' information or serve their ploys.
You can read this my article for hiding your Joomla back-end or use my plugin called V4 Security (support Joomla 3.x, 2.x). You can download it here. Below are its features and illustrate images.
You also can set a Redirect URL if someones go to the URL your_site/administrator (without token). I think you should set an URL of a 404 page here.
If you enable this function and specify Max attempts number here (e.g. 3), any user will be locked after 3 times of failed login.
Hope this plugin can help you have well sleep when running Joomla -:)
Do you have any things else? Any comment is welcome.
You can read this my article for hiding your Joomla back-end or use my plugin called V4 Security (support Joomla 3.x, 2.x). You can download it here. Below are its features and illustrate images.
1. Backend Protection
If you key Login Token here (e.g. hung123, you must access your back-end via a URL like: your_site/administrator/?hung123).You also can set a Redirect URL if someones go to the URL your_site/administrator (without token). I think you should set an URL of a 404 page here.
2. Login Attempts
If you enable this function and specify Max attempts number here (e.g. 3), any user will be locked after 3 times of failed login.
3. Password Complexity
In this function, you will config for the password rule in your web site. You can select to apply on Frontend, Backend or both. This function may be useful if you use Joomla to build a social network or an intranet for your company.Hope this plugin can help you have well sleep when running Joomla -:)
Do you have any things else? Any comment is welcome.
Monday, June 2, 2014
How to find the biggest table in MS SQL
If you need to find out the biggest table in MS SQL, you can use below command:
SELECT
t.NAME AS TableName,
i.name as indexName,
sum(p.rows) as RowCounts,
sum(a.total_pages) as TotalPages,
sum(a.used_pages) as UsedPages,
sum(a.data_pages) as DataPages,
(sum(a.total_pages) * 8) / 1024 as TotalSpaceMB,
(sum(a.used_pages) * 8) / 1024 as UsedSpaceMB,
(sum(a.data_pages) * 8) / 1024 as DataSpaceMB
FROM
sys.tables t
INNER JOIN
sys.indexes i ON t.OBJECT_ID = i.object_id
INNER JOIN
sys.partitions p ON i.object_id = p.OBJECT_ID AND i.index_id = p.index_id
INNER JOIN
sys.allocation_units a ON p.partition_id = a.container_id
WHERE
t.NAME NOT LIKE 'dt%' AND
i.OBJECT_ID > 255 AND
i.index_id <= 1
GROUP BY
t.NAME, i.object_id, i.index_id, i.name
ORDER BY
--object_name(i.object_id) -- sort by id
--SUM(p.rows) DESC -- sort by number of rows
SUM(a.total_pages) DESC -- sort by TotalSpaceMB
Thanks for the instruction from marc_s guy here.
SELECT
t.NAME AS TableName,
i.name as indexName,
sum(p.rows) as RowCounts,
sum(a.total_pages) as TotalPages,
sum(a.used_pages) as UsedPages,
sum(a.data_pages) as DataPages,
(sum(a.total_pages) * 8) / 1024 as TotalSpaceMB,
(sum(a.used_pages) * 8) / 1024 as UsedSpaceMB,
(sum(a.data_pages) * 8) / 1024 as DataSpaceMB
FROM
sys.tables t
INNER JOIN
sys.indexes i ON t.OBJECT_ID = i.object_id
INNER JOIN
sys.partitions p ON i.object_id = p.OBJECT_ID AND i.index_id = p.index_id
INNER JOIN
sys.allocation_units a ON p.partition_id = a.container_id
WHERE
t.NAME NOT LIKE 'dt%' AND
i.OBJECT_ID > 255 AND
i.index_id <= 1
GROUP BY
t.NAME, i.object_id, i.index_id, i.name
ORDER BY
--object_name(i.object_id) -- sort by id
--SUM(p.rows) DESC -- sort by number of rows
SUM(a.total_pages) DESC -- sort by TotalSpaceMB
Thanks for the instruction from marc_s guy here.
Monday, May 12, 2014
Google Drive: notify CRUD (created, updated, deleted) files in folders
Google Drive is a good place to store files and share them with your friends or within your company. Google also developed notification mechanism for spreadsheets when changes are made to them. However that isn't enough. Users don't have only spreadsheets , they also have many types of documents. So they very need a tool to notify when these documents are changes. Many users already asked for this feature here. While waiting Google develops this feature, there is a good guy (Marcello Scacchetti from Jelly Bend) contributed a Google Apps Scripts to monitor new or deleted files in folders of Google Drive. It works like Microsoft's SharePoint. You can read and copy his code here.
In this article, I will share my modification on his code to make some additional capacities as below:
All things which you can do are:
1. Go to menu Drive Folder Monitor >> Configuration, then add the folders which you want to monitor and select time for interval running at Run drive folder monitor each box. Currently it just supports top level folders. I'll add a new version to support sub folders when I have time. First running, Google may ask you to authorize the script, pls click Accept.
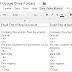
2. Change Email To Inform (cell A2) to emails (separated by commas) which you want to send notifications.
3. Change Email Title of New Documents (cell B2), Email Title of Updated Documents (cell C2), Email Title of New Documents (cell D2) for the subject of each type of notification email.
4. Change Email Body (cell B3, C3, D3) for the content of each type of notification email. Remember don't delete $$FILE$$ string. It will be replaced by folders and files which are changed.
5. Configure Excluded Folders (cell B4), the format of folder is TOP_FOLDER/SUB_FOLDER (slash between folders), folders are separated by commas (,).
6. This tool will run automatically with interval time you set in step 1. In the case of you want to run manually, let click menu Drive Folder Monitor >> Run monitor folder.
Hope you can use this script in your work. Any comment and contribution idea are welcome.
Best regards,
Hung
In this article, I will share my modification on his code to make some additional capacities as below:
- Notify updated files
- Able to configure list of emails to receive notifications instead of only owner
- Able to configure subject and content of notification email for each of notification type (new, updated, deleted)
- Able to configure excluded folders (don't send notification if changed files are in these folders).
All things which you can do are:
1. Go to menu Drive Folder Monitor >> Configuration, then add the folders which you want to monitor and select time for interval running at Run drive folder monitor each box. Currently it just supports top level folders. I'll add a new version to support sub folders when I have time. First running, Google may ask you to authorize the script, pls click Accept.
2. Change Email To Inform (cell A2) to emails (separated by commas) which you want to send notifications.
3. Change Email Title of New Documents (cell B2), Email Title of Updated Documents (cell C2), Email Title of New Documents (cell D2) for the subject of each type of notification email.
4. Change Email Body (cell B3, C3, D3) for the content of each type of notification email. Remember don't delete $$FILE$$ string. It will be replaced by folders and files which are changed.
5. Configure Excluded Folders (cell B4), the format of folder is TOP_FOLDER/SUB_FOLDER (slash between folders), folders are separated by commas (,).
6. This tool will run automatically with interval time you set in step 1. In the case of you want to run manually, let click menu Drive Folder Monitor >> Run monitor folder.
Hope you can use this script in your work. Any comment and contribution idea are welcome.
Best regards,
Hung
Thursday, May 8, 2014
MS SQL Server 2014: 5 important new or enhanced features
Microsoft have released SQL Server 2014 with many enhanced features comparing with old versions. In this article, I'll introduce 5 new important features that you can consider to upgrade for your organization.
Basically, this feature requires a SSD disk to host its extension file. The performance is very depended on SSD, some manufacturers have optimized their product to use with SQL Server 2014 (e.g. Fusion) so their product can get better performance.
To enable this feature, you can use the following command:
ALTER SERVER CONFIGURATION
SET BUFFER POOL EXTENSION ON
(
FILENAME = 'D:\BufferPoolExtensionFile.BPE',
SIZE = 40 GB
)
GO
In which, D is SSD, min of SIZE = max_server_memory configuration, an optimal ratio SIZE:max_server_memory is 4:1 to 8:1.
To check buffer pool configuration, run:
SELECT path, file_id, state, state_description, current_size_in_kb
FROM sys.dm_os_buffer_pool_extension_configuration;
Its Resource Governor provides a new capability to manage application storage I/O utilization. First introduced with SQL Server 2008, the Resource Governor originally enabled you to limit the amount of CPU and memory that a given workload can consume. Now SQL Server 2014 extends the reach of the Resources Governor so that you can now manage storage I/O usage as well. The SQL Server 2014 Resource Governor can limit the physical I/Os issued for user threads in a given resource pool, allowing you to have more predictable application performance.
SQL Server 2014 also supports new Storage Spaces feature of Windows Server 2012. With Storage Spaces, you can create pools of tiered storage to improve application availability and performance. In addition, SQL Server 2014 can take advantage of Server Message Block (SMB) 3.0 enhancements to achieve high-performance database storage on Windows Server 2012 R2 and Windows Server 2012 file shares. Many enhancements were made to SMB 3.0, with the most notable being SMB Transparent Failover and SMB Direct. The new SMB Transparent Failover feature provides highly reliable SMB storage that's fully supported for applications like SQL Server and Hyper-V. With the new SMB Direct feature, you can leverage the NIC's Remote Direct Memory Access (RDMA) feature to provide access speeds for SMB file shares nearing the access speed for local resources.
Do you think what else? All comments are welcome.
1. Buffer Pool Extensions
No doubt, it is the most significant new feature of SQL Server 2014, especially it is available for Standard 64 bit version. It is recommended for write-heavy applications. I have tested it, it helps to increase 30% - 50% writing performance, for reading (select) it seems can't help much. Below is the illustration of high-level architectural overview of the buffer pool relative to other SQL Server components.Basically, this feature requires a SSD disk to host its extension file. The performance is very depended on SSD, some manufacturers have optimized their product to use with SQL Server 2014 (e.g. Fusion) so their product can get better performance.
To enable this feature, you can use the following command:
ALTER SERVER CONFIGURATION
SET BUFFER POOL EXTENSION ON
(
FILENAME = 'D:\BufferPoolExtensionFile.BPE',
SIZE = 40 GB
)
GO
In which, D is SSD, min of SIZE = max_server_memory configuration, an optimal ratio SIZE:max_server_memory is 4:1 to 8:1.
To check buffer pool configuration, run:
SELECT path, file_id, state, state_description, current_size_in_kb
FROM sys.dm_os_buffer_pool_extension_configuration;
2. In-Memory OLTP Engine
It is also know in formerly project Hekaton of Microsoft. This feature is available only for Enterprise 64 bit version. By moving tables and stored procedures used frequently into memory, it reduces I/O and improve performance of your OLTP applications. Microsoft states that some applications can expect up to a 30x performance improvement. However, this feature just supports limited types of data, so you may need to re-design your tables and stored procedures to load them into memory. It is not an easy work. I have tested this feature and seen that it helps increasing 4x performance in my case with heavy processing data. In the case I do a simple query and get just 1 row data, it is slower than normal. So be careful what you should put into the memory.3. Columnstore Indexes For All
It is first introduced in SQL Server 2012 to provide significantly improved performance for data warehousing types of queries. Microsoft states that for some types of queries, columnstore indexes can provide up to 10x performance improvements. However, in the original implementation of the columnstore indexes, the underlying table had to be read-only. SQL Server 2014 eliminates this restriction. The new updateable columnstore index enables updates to be performed to the underlying table without first needing to drop the columnstore index. A SQL Server 2014 columnstore index must use all of the columns in the table, and it can't be combined with other indexes.4. Windows Server 2012 Integration
SQL Server 2014 enhances integration with Windows Server 2012 as also as Windows Server 2012 R2. SQL Server 2014 Enterprise will have the ability to scale up to 640 logical processors and 4TB of memory in a physical environment (128GB for SQL Server 2014 Standard ). In the case of using virtual machine, it can scale up to 64 virtual processors and 1TB of memory.Its Resource Governor provides a new capability to manage application storage I/O utilization. First introduced with SQL Server 2008, the Resource Governor originally enabled you to limit the amount of CPU and memory that a given workload can consume. Now SQL Server 2014 extends the reach of the Resources Governor so that you can now manage storage I/O usage as well. The SQL Server 2014 Resource Governor can limit the physical I/Os issued for user threads in a given resource pool, allowing you to have more predictable application performance.
SQL Server 2014 also supports new Storage Spaces feature of Windows Server 2012. With Storage Spaces, you can create pools of tiered storage to improve application availability and performance. In addition, SQL Server 2014 can take advantage of Server Message Block (SMB) 3.0 enhancements to achieve high-performance database storage on Windows Server 2012 R2 and Windows Server 2012 file shares. Many enhancements were made to SMB 3.0, with the most notable being SMB Transparent Failover and SMB Direct. The new SMB Transparent Failover feature provides highly reliable SMB storage that's fully supported for applications like SQL Server and Hyper-V. With the new SMB Direct feature, you can leverage the NIC's Remote Direct Memory Access (RDMA) feature to provide access speeds for SMB file shares nearing the access speed for local resources.
5. Enhanced AlwaysOn Availability Groups
This feature has been enhanced with support for additional secondary replicas and Windows Azure integration. First introduced with SQL Server 2012, AlwaysOn Availability Groups boosted SQL Server availability by providing the ability to protect multiple databases with up to four secondary replicas. In SQL Server 2014, Microsoft has enhanced AlwaysOn integration by expanding the maximum number of secondary replicas from four to eight. Readable secondary replicas are now available for read-only workloads, even when the primary replica is unavailable. SQL Server 2014 also provides Windows Azure AlwaysOn integration. This new integration feature enables you to create asynchronous availability group replicas in Windows Azure for disaster recovery. In the event of a local database outage, you can run your SQL Server databases from Windows Azure VMs. The new Windows Azure AlwaysOn availability options are fully integrated into SQL Server Management Studio (SSMS).Do you think what else? All comments are welcome.
Tuesday, April 15, 2014
Solving Heartbleed Bug
Earlier this week, security researchers announced a vulnerability (known as “Heartbleed Bug”) in OpenSSL, a widely-used opensource cryptographic software library. It can allow attackers to read the memory of the systems using vulnerable versions of OpenSSL library (1.0.1 through 1.0.1f). This may disclose the secret keys of vulnerable servers, which allows attackers to decrypt and eavesdrop on SSL encrypted communications and impersonate service providers. In addition, other data in memory may be disclosed, which could include usernames and passwords of users or other data stored in server memory.
To be clear, this is a vulnerability of the OpenSSL library, and not a flaw with SSL/TLS, nor certificates issued by Symantec or GeoTrust.
Here are steps to fix this bug:
- Identify if your web servers are vulnerable (running OpenSSL versions 1.0.1 through 1.0.1f with heartbeat extension enabled). If you’re running a version of OpenSSL prior to 1.0.1, no further action is required.
- If your server is impacted, update to the latest patched version of OpenSSL (1.0.1g).
- Generate a new Certificate Signing Request (CSR).
- Reissue any SSL certificates for affected web servers using the new CSR (do this after moving to a patched version of OpenSSL).
- Install the new SSL certificate.
- Website administrators should also consider resetting end-user passwords that may have been visible in a compromised server memory.
Hope you will save in this storm.
Thursday, April 10, 2014
MySQL: manage (disable, purge/clean) binary log files (mysql-bin.xxx)
MySQL binary log files contain all statements that update data or potentially could have updated it.
These files have 2 important purposes:
I suggest 2 ways for handling them.
1. Disable these binary logs if you don't use replication function.
Open my.ini (Windows) or my.cnf (Linux), then find the line (starting with log-bin or log_bin) and comment to disable it:
#log-bin = mysql-bin
You should create a backup (dump data) daily if disable this.
2. Purge / clean them frequently if you use replication function.
Login to mysql then use the following command:
You may also need to set expire_logs_days value:
And add or modify this variable in my.ini (Windows) or my.cnf (Linux).
To avoid to interrupt your replication, run SHOW SLAVE STATUS\G to check, you will see 2 binary logs from the Master: Master_Log_File and Relay_Master_Log_File. Then run this command:
PURGE BINARY LOGS TO 'Whatever Relay_Master_Log_File Is';
Finally you should restart your MySQL. That's all.
These files have 2 important purposes:
- Data Recovery : after a backup file has been restored, the events in the binary log that were recorded after the backup was made are re-executed. These events bring databases up to date from the point of the backup.
- High availability / replication : used on master replication servers as a record of the statements to be sent to slave servers. The master server sends the events contained in its binary log to its slaves, which execute those events to make the same data changes that were made on the master.
I suggest 2 ways for handling them.
1. Disable these binary logs if you don't use replication function.
Open my.ini (Windows) or my.cnf (Linux), then find the line (starting with log-bin or log_bin) and comment to disable it:
#log-bin = mysql-bin
You should create a backup (dump data) daily if disable this.
2. Purge / clean them frequently if you use replication function.
Login to mysql then use the following command:
mysql> PURGE BINARY LOGS BEFORE DATE(NOW() - INTERVAL 3 DAY) + INTERVAL 0 SECOND;You may also need to set expire_logs_days value:
mysql> SET GLOBAL expire_logs_days = 3;And add or modify this variable in my.ini (Windows) or my.cnf (Linux).
[mysqld]
expire-logs-days=3To avoid to interrupt your replication, run SHOW SLAVE STATUS\G to check, you will see 2 binary logs from the Master: Master_Log_File and Relay_Master_Log_File. Then run this command:
PURGE BINARY LOGS TO 'Whatever Relay_Master_Log_File Is';
Finally you should restart your MySQL. That's all.
Monday, April 7, 2014
Setup free emails with your own domain on Outlook.com
MS Outlook.com offers free email service, in which you can create emails (50 & can more) with your own domain. Further its email is unlimited storage. So what are you waiting for? :)
Go to DNS of the domain and add a MX record with value same as MX server which you see on Mail setup (required) the area. You can add your domain registrar for supporting to add this MX record.
When this is finished, it needs time (few minutes to 48 hours) to verify your domain. After click Refresh in above picture, if you see Your service is Active like the following picture, that's time you can add emails for the domain:
Or after few hours, you can sign-in domains.live.com again, then select your domain with status Pending DNS configuration to hit Refresh button again, until it is active.
Then click Connect devices and apps with POP:
Click Enable option, select Don't let... to keep your emails on the server. Click Save button.
1. Register your own domain with domains.live.com
Go to domains.live.com, sign in then click Add domain button. Fill your domain to the box then click Continue button. See below image for quick reference:2. Review and accept agreement
Microsoft will ask you review & accept the agreement. Let accept it.3. Verify your domain and config MX record
After finishing step 2 above, it will display setting info for you to config your domain. You must verify the domain before using. There are some ways there. I recommend you use MX record way to verify and config your domain to send emails just in 1 step. Let pay attention on Mail setup (required) section as the following:Go to DNS of the domain and add a MX record with value same as MX server which you see on Mail setup (required) the area. You can add your domain registrar for supporting to add this MX record.
When this is finished, it needs time (few minutes to 48 hours) to verify your domain. After click Refresh in above picture, if you see Your service is Active like the following picture, that's time you can add emails for the domain:
Or after few hours, you can sign-in domains.live.com again, then select your domain with status Pending DNS configuration to hit Refresh button again, until it is active.
4. Create accounts (emails)
After your domain is active, you can create emails. Or you can add them by clicking Member accounts menu then click Add button. You also can Edit or Delete emails here.5. Check and send emails via an apps
If you have time, you can read detail instruction here. In this article, I'll brief in major steps:5.1 Enable POP
Go to Outlook.com, log-in to your email account, then click Options:Click Enable option, select Don't let... to keep your emails on the server. Click Save button.
5.2 Config client email app
After enabling POP, now you can receive & send emails via an apps. Below is setting info:-
Incoming (POP3) Server
-
Server address: pop-mail.outlook.com
-
Port: 995
-
Encrypted Connection: SSL
-
-
Outgoing (SMTP) Server
-
Server address: smtp-mail.outlook.com
-
Port: 25 (or 587 if 25 is blocked)
-
Authentication: Yes
-
Encrypted Connection: TLS
-
-
User name: Your email address
-
Password: Your password
-
If you don’t want email to be deleted from your Outlook.com inbox after it’s downloaded to your email app, select the Leave a copy of messages on the server option.
That's all. Bye! See you in next geek!
Thursday, March 27, 2014
Review email services for own domain
A good email service is very important for your business and also for your online life. How about your current email service? did you lose any email? did it run smoothly? how much does it cost you?
It's time to look around email services for finding your best email service for your own domain.
Free emails: 50
Price: $19.95/email account/year to remove ads
Storage: unlimited
Attachment: up to 25 MB
Free emails: None
Price: $50/email account/year
Storage: 30 GB
Attachment: up to 25 MB
Free emails: None
Price: $60/email account/year
Storage: 50 GB
Attachment: up to 25 MB
Free emails: None
Price: $35/email account/year
Storage: unlimited
Attachment: up to 20 MB
Free emails: None
Price: start form $10/email account/year
Storage: start from 250 MB
Attachment: up to 20 MB
Free emails: None
Price: $24/email account/year
Storage: 25 GB
Attachment: up to 50 MB
Free emails: 20
Price: $24/email account/year
Storage: from 5 GB (free)
Attachment: depend
Hope you can select the best email service for your own domain.
It's time to look around email services for finding your best email service for your own domain.
1. Outlook.com
I really love it, it is a profuct of Microsoft which is the last guy in top big buys still gives free emails. To register, you must set up your domain on http://domains.live.comFree emails: 50
Price: $19.95/email account/year to remove ads
Storage: unlimited
Attachment: up to 25 MB
2. Google Apps
I used it for many my domains. This guy is leading in email services, but Google Apps stops to give free emails from 2012. Really sad for that.Free emails: None
Price: $50/email account/year
Storage: 30 GB
Attachment: up to 25 MB
3. Office 365 Small Business
Another guy from Microsoft beside Outlook.com. This guy is main competitor of Google Apps.Free emails: None
Price: $60/email account/year
Storage: 50 GB
Attachment: up to 25 MB
4. Yahoo Small Business
Yahoo still is one of the leaders in email service. Before Gmail, I just use Yahoo! Mail. Now I still keep my Yahoo! Mail for some my contacts and Yahoo! Messenger.Free emails: None
Price: $35/email account/year
Storage: unlimited
Attachment: up to 20 MB
5. FastMail
Owned by Opera, FastMail is the most popular alternate to Google Apps for email service on the own domain for years now because some good reasons. Cheap, stability, fast.Free emails: None
Price: start form $10/email account/year
Storage: start from 250 MB
Attachment: up to 20 MB
6. Rackspace Email
Between tons of hosting providers sell email service, Rackspace is one of the best guys.Free emails: None
Price: $24/email account/year
Storage: 25 GB
Attachment: up to 50 MB
7. Zoho Mail
Zoho is famous guy in CRM. However he is also big player in email service. Especially, it give 5 free users.Free emails: 20
Price: $24/email account/year
Storage: from 5 GB (free)
Attachment: depend
Hope you can select the best email service for your own domain.
Thursday, March 20, 2014
Detect and remove SPAM SEO (BlackHat SEO)
Today using SPAM SEO (Black Hat SEO) is a stupid way to get higher ranking in Google. The website uses SPAM SEO is detected easily by Google and Google will shoot penalty the website if it detects many SPAM SEO for the website.
However this is the best way to knock out a competitor. The competitor will take much time to work with Google and remove / disavow these SPAM SEO links. It is not an easy work.
So your website may become a victim of bad guy for his cruel purpose.
1. How to know if my website gets Malware Spam SEO (MW:SPAM:SEO)
You can do one of the following way:
-Install an antivirus like Avas, AVG, etc. on a computer, then browse your website. It will alert if your website infects MW:SPAM:SEO.
-Scan your website via sitecheck2.sucuri.net. It will alert and point out where MW:SPAM:SEO appears on your website. Although it just makes highlights the MW:SPAM:SEO on HTML code, but it will help you to find out where the Malware comes in the source code of your website. I recommend this tool.
2. How to know where MW:SPAM:SEO stays in the source code
2.1 Use antivirus software to scan your source code files. Normally, some antivirus software can detect infected / compromised files. This is fastest way to remove the Malware if its code pattern is in a database of an antivirus.
2.2 Sort files by created / modified date to limit files or make priorities on files for exploring.
2.3 Check & sort by date your web server log on POST requests if you have configured the log. It will help a lot to limit files or make priorities on files for exploring the Malware manually.
2.4 Based on scanning result of sitecheck2.sucuri.net, you can know which page then guess which file can be infected.
2.5 Search special phrases
-Some popular malwares can have a special phrases to find out. e.g. Clickjack will have function dnnViewState or function xViewState. So just do a search on these famous phrases and see if you are lucky.
-After doing above steps, and you still cannot find where the Malware stays. It's time to do some hard works. It will take your time depending on your experiences. If your source code is written by PHP, search special functions of PHP such as: eval, base64_decode, gzinflate, str_rot13, hexdec, file_get_contents, mail, fsockopen, pfsockopen, stream_socket_client, exec, system, passthru. For example, if your server is Linux you can use below command to find all files containing eval or base64_decode function then export these file names to forexploring.txt file:
find . -type f -name '*.php' | xargs egrep -i "(eval|base64_decode) *\(" > forexploring.txt
In my real case, I have 2 websites infected MW:SPAM:SEO. One website infect Clickjack, then I remove it easily by searching function dnnViewState mentioned in step 2.5 above. Another website I tried to scan with some antivirus as also as searching keywords of popular malwares but not found. Then I use step 2.4 above, then I guess that it can be in a free module which I installed in my Joomla website. The module is mod_InowSlideShow. After that I search special functions of PHP in the source files of this module, and I found the file modules\mod_InowSlideShow\tmpl\default.php use function file_get_contents to insert a HTML code to my site. I removed it, then didn't get any warning after doing step 1 again.
3. Prevention is better than cure
-Update frequently security fixes for your server (OS, web server, DB server, PHP etc)
-Update frequently security fixes for your CMS (Joomla, WordPress etc)
-Set up an antivirus on your server, set up firewall on your server
-Set up logs for your server
-Change your passwords frequently and follow password name rule
Good luck to you!
However this is the best way to knock out a competitor. The competitor will take much time to work with Google and remove / disavow these SPAM SEO links. It is not an easy work.
So your website may become a victim of bad guy for his cruel purpose.
1. How to know if my website gets Malware Spam SEO (MW:SPAM:SEO)
You can do one of the following way:
-Install an antivirus like Avas, AVG, etc. on a computer, then browse your website. It will alert if your website infects MW:SPAM:SEO.
-Scan your website via sitecheck2.sucuri.net. It will alert and point out where MW:SPAM:SEO appears on your website. Although it just makes highlights the MW:SPAM:SEO on HTML code, but it will help you to find out where the Malware comes in the source code of your website. I recommend this tool.
2. How to know where MW:SPAM:SEO stays in the source code
2.1 Use antivirus software to scan your source code files. Normally, some antivirus software can detect infected / compromised files. This is fastest way to remove the Malware if its code pattern is in a database of an antivirus.
2.2 Sort files by created / modified date to limit files or make priorities on files for exploring.
2.3 Check & sort by date your web server log on POST requests if you have configured the log. It will help a lot to limit files or make priorities on files for exploring the Malware manually.
2.4 Based on scanning result of sitecheck2.sucuri.net, you can know which page then guess which file can be infected.
2.5 Search special phrases
-Some popular malwares can have a special phrases to find out. e.g. Clickjack will have function dnnViewState or function xViewState. So just do a search on these famous phrases and see if you are lucky.
-After doing above steps, and you still cannot find where the Malware stays. It's time to do some hard works. It will take your time depending on your experiences. If your source code is written by PHP, search special functions of PHP such as: eval, base64_decode, gzinflate, str_rot13, hexdec, file_get_contents, mail, fsockopen, pfsockopen, stream_socket_client, exec, system, passthru. For example, if your server is Linux you can use below command to find all files containing eval or base64_decode function then export these file names to forexploring.txt file:
find . -type f -name '*.php' | xargs egrep -i "(eval|base64_decode) *\(" > forexploring.txt
In my real case, I have 2 websites infected MW:SPAM:SEO. One website infect Clickjack, then I remove it easily by searching function dnnViewState mentioned in step 2.5 above. Another website I tried to scan with some antivirus as also as searching keywords of popular malwares but not found. Then I use step 2.4 above, then I guess that it can be in a free module which I installed in my Joomla website. The module is mod_InowSlideShow. After that I search special functions of PHP in the source files of this module, and I found the file modules\mod_InowSlideShow\tmpl\default.php use function file_get_contents to insert a HTML code to my site. I removed it, then didn't get any warning after doing step 1 again.
3. Prevention is better than cure
-Update frequently security fixes for your server (OS, web server, DB server, PHP etc)
-Update frequently security fixes for your CMS (Joomla, WordPress etc)
-Set up an antivirus on your server, set up firewall on your server
-Set up logs for your server
-Change your passwords frequently and follow password name rule
Good luck to you!
Tuesday, February 11, 2014
.Net solving error: Call was rejected by callee
If your program uses MS Office Application Interop (e.g. Microsoft.Office.Interop.Word.Document) to procedure documents , sometimes you may get this following error:
Call was rejected by callee. (Exception from HRESULT: 0x80010001 (RPC_E_CALL_REJECTED))
It happens only in few documents and the others will not. To solve this problem, we have 2 ways:
Way 1: Turn off all grammar / spelling functions, for example: open MS Word and go to Options, uncheck options:
+Check spelling as you type
+Use contextual spelling
+Mark grammar errors as you type
+Check grammar with spelling
Way 2: if you develop the program, you can add some codes to turn off grammar / spelling functions, for example in C#:
CurrentDocument.ShowGrammaticalErrors = false;
CurrentDocument.ShowRevisions = false;
CurrentDocument.ShowSpellingErrors = false;
Hope you save a tablet for headache.
Call was rejected by callee. (Exception from HRESULT: 0x80010001 (RPC_E_CALL_REJECTED))
It happens only in few documents and the others will not. To solve this problem, we have 2 ways:
Way 1: Turn off all grammar / spelling functions, for example: open MS Word and go to Options, uncheck options:
+Check spelling as you type
+Use contextual spelling
+Mark grammar errors as you type
+Check grammar with spelling
Way 2: if you develop the program, you can add some codes to turn off grammar / spelling functions, for example in C#:
CurrentDocument.ShowGrammaticalErrors = false;
CurrentDocument.ShowRevisions = false;
CurrentDocument.ShowSpellingErrors = false;
Hope you save a tablet for headache.
Thursday, January 9, 2014
Joomla: control all types of redirection and http error codes with single component
Does your Joomla website has some links (URLs) needing to redirect? You can use Redirect core component of Joomla. However, it just does 1 type 301 redirection (Moved Permanently) and doesn't support to redirect URLs with Regular Expressions.
Luckily, we have a free component which allows you control almost types of redirection and http error codes. This below inforgraphic of SEOmoz can help you understand them and how they are important in SEO.
So what is the component? It's ReDJ component. You can check out it here. The following is its features:
+Manage redirection URLs, support macros & regular expressions for URLs
+Support to define 404 page quickly
+Support to statistic http error codes which are got and their visited URLs
+Support to statistic referrer URLs
And you can use it to:
+Solve SEO problems
+Create short URLs and use them with your domain (like they are created from bitly.com)
THE END ./.
Luckily, we have a free component which allows you control almost types of redirection and http error codes. This below inforgraphic of SEOmoz can help you understand them and how they are important in SEO.
So what is the component? It's ReDJ component. You can check out it here. The following is its features:
+Manage redirection URLs, support macros & regular expressions for URLs
+Support to define 404 page quickly
+Support to statistic http error codes which are got and their visited URLs
+Support to statistic referrer URLs
And you can use it to:
+Solve SEO problems
+Create short URLs and use them with your domain (like they are created from bitly.com)
THE END ./.
Saturday, January 4, 2014
Oracle: connect as sysdba without db user password
Oracle allows you connect as SYSDBA, if your Windows user is a member of 'ORA_sid_DBA' or 'ORA_DBA' group. Below are steps to do that:
1. Log in Windows as administrator
2. Check if your Windows has 'ORA_DBA' group. If not, let create it
3. Add your Windows user to 'ORA_DBA' group
4. Run TNSPING tool to check where SQLNET.ORA file is located, like the following:
1. Log in Windows as administrator
2. Check if your Windows has 'ORA_DBA' group. If not, let create it
3. Add your Windows user to 'ORA_DBA' group
4. Run TNSPING tool to check where SQLNET.ORA file is located, like the following:
C:\>tnsping orcl TNS Ping Utility for 32-bit Windows: Version 10.2.0.4.0 - Production on 09-JUN-2009 14:50:20 Copyright (c) 1997, 2007, Oracle. All rights reserved. Used parameter files: C:\oracle\product\10.2.0\db_1\NETWORK\ADMIN\sqlnet.ora
5. Add or remove comment for the following line:SQLNET.AUTHENTICATION_SERVICES = (NTS)6. Re-login Windows with the user mentioned above, try this line:C:\>sqlplus / as sysdba
7. Then see if you can login successfully
Subscribe to:
Posts (Atom)